Cybersecurity
 www.buskill.in
www.buskill.in
Today we're ecstatic to [publish our first demo](https://www.buskill.in/3d-print-2024-05/) showing a homemade BusKill Cable (in the prototype 3D-printed case) triggering a lockscreen. | [](https://www.buskill.in/3d-print-2024-05/) | |:--:| | *Watch the [3D-Printed USB Dead Man Switch (Prototype Demo)](https://www.youtube.com/v/vFTQatw94VU) for more info [youtube.com/v/vFTQatw94VU](https://www.youtube.com/v/vFTQatw94VU)* | via [@Goldfishlaser@lemmy.ml](https://lemmy.ml/u/Goldfishlaser) In our [last update](https://www.buskill.in/3d-print-2023-08/), I showed a video demo where I successfully triggered a lockscreen using a BusKill prototype without the 3D-printed body for the case and N35 disc magnets. I realized that the N35 disc magnets were not strong enough. In this update, I show a demo with the prototype built inside a 3D-printed case and with (stronger) N42 and N52 cube magnets. # What is BusKill? BusKill is a laptop kill-cord. It's a USB cable with a magnetic breakaway that you attach to your body and connect to your computer. | [](https://www.buskill.in/#demo) | |:--:| | *Watch the [BusKill Explainer Video](https://www.buskill.in/#demo) for more info [youtube.com/v/qPwyoD_cQR4](https://www.youtube.com/v/qPwyoD_cQR4)* | If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys -- thus keeping your encrypted data safe from thieves that steal your device. # Why? While [we do what we can](https://www.buskill.in//buskill-onion-service-tor/) to allow at-risk folks to [purchase BusKill cables anonymously](https://www.buskill.in//bitcoin-black-friday-2023/#privacy), there is always the risk of [interdiction](https://docs.buskill.in/buskill-app/en/stable/faq.html#q-what-about-interdiction). We don't consider hologram stickers or tamper-evident tape/crisps/glitter to be sufficient solutions to supply-chain security. Rather, the solution to these attacks is to build open-source, easily inspectable hardware whose integrity can be validated without damaging the device and without sophisticated technology. Actually, the best way to confirm the integrity of your hardware is to build it yourself. Fortunately, BusKill doesn't have any circuit boards, microcontrollers, or silicon; it's trivial to print your own BusKill cable -- which is essentially a USB extension cable with a magnetic breakaway in the middle Mitigating interdiction via 3D printing is one of many reasons that [Melanie Allen](https://github.com/Goldfishlaser) has been diligently working on prototyping a 3D-printable BusKill cable this year. In this article, we hope to showcase her progress and provide you with some OpenSCAD and `.stl` files you can use to build your own version of the prototype, if you want to help us test and improve the design. # Print BusKill [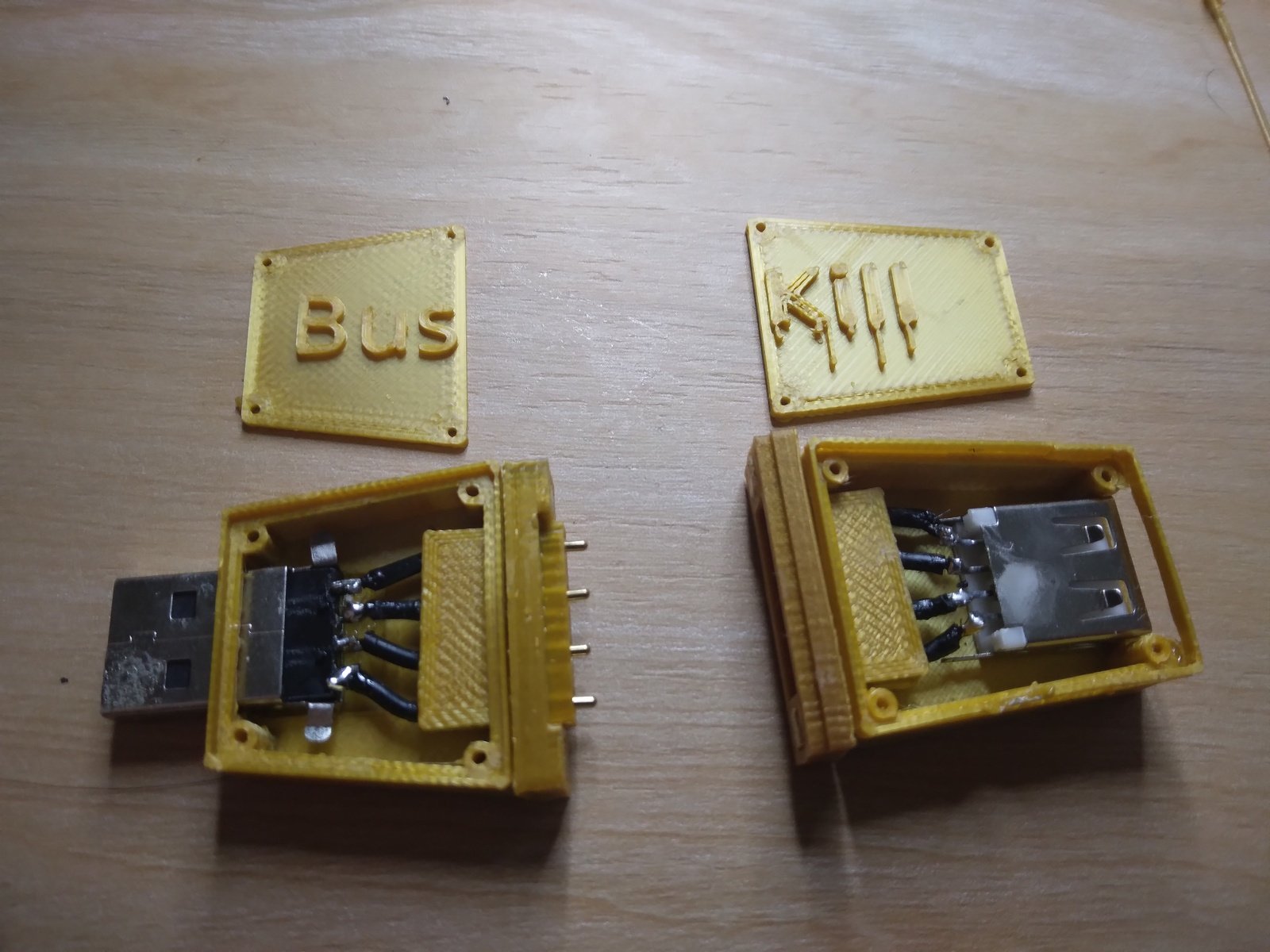](https://www.buskill.in/3d-print-2024-05/) If you'd like to reproduce our experiment and print your own BusKill cable prototype, you can [download the stl files](https://www.buskill.in/3d-print-2024-05/) and [read our instructions](https://www.buskill.in/3d-print-2024-05/) here: * [buskill.in/3d-print-2024-05](https://www.buskill.in/3d-print-2024-05/) # Iterate with us! **If you have access to a 3D Printer, you have basic EE experience, or you'd like to help us test our 3D printable BusKill prototype, please** [let us know](https://buskill.in/contact). The whole is greater than the sum of its parts, and we're eager to finish-off this 3D printable BusKill prototype to help make this security-critical tool accessible to more people world-wide!
 www.techfinitive.com
www.techfinitive.com
Davey Winder provides details of the LabHost bust by British police in partnership with Microsoft and others - and explains LabHost's modus operandi
In the last blog we talked about what everyone assumed was the most boring topic that you could talk about, keeping your dependencies up to date. But I think I’ve got it topped this time, this time we are going to be talking about that number one thing that all developers love spending their time working on... Logging.
The differences between application security and developer security are simple enough in principle, but go significantly further as soon as you get past the surface. Many people in the cyber security community seem to place a great emphasis on the effectiveness of application security but in many cases, will completely negate the secondary portion of this which is securing the individual who is responsible for introducing security bugs to the software. I'm not saying that to be harsh, mistakes are a simple part of life and without the proper tooling and education it is very easy to continue to produce mistakes especially when greeted with constricted timelines and consistent budget crunch.
It is common for companies to neglect financing in cyber security for a quick short term gain. And at the same time the laws are created such that an offensive hacker would be the criminal. By turning the law around the blame would be on the company for building insecure systems, just like it is right now companies get problems if they would create unsafe products for consumers. What do you think would happen if laws would change in such a way, that gaining unauthorized access would become legal? Note that I've intentionally excluded permission to share sensitive information. Would love to read your responses and thoughts
